Expired Domains



Finding expired domains
By using expired domains we can mimic a legit website and forge other information to make our malicious domain seem legit.
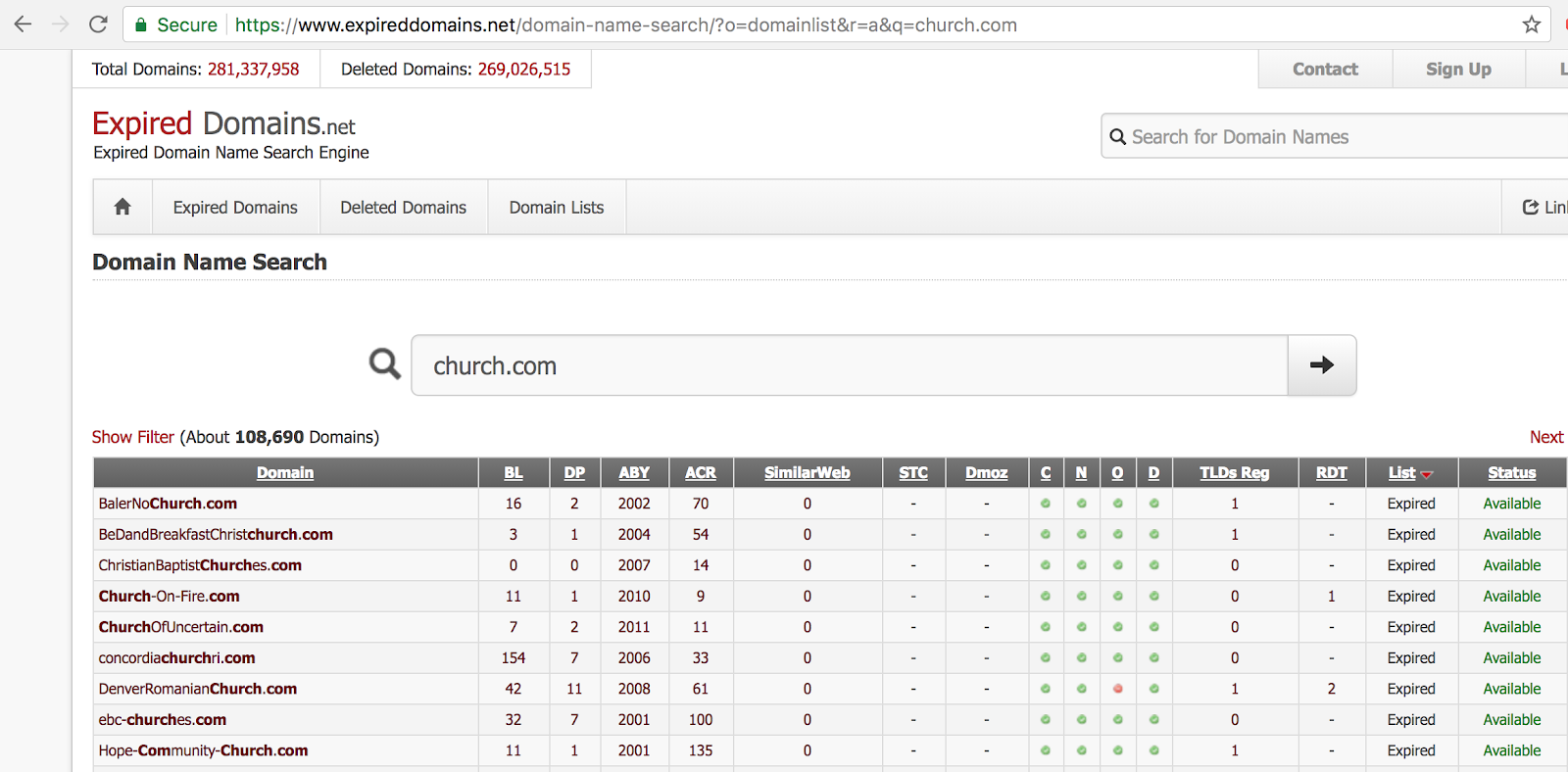
There are several websites that can be used to find expired domains. There are also a few open source tools that allow you to locate expired domains.
I will be searching for domains that have the word church in their name. Hiding behind innocent domains that act as churches, medical help, education, or other related things can help cover a malicious domain.
We can see the domain “hope-community-church.com”
Domain Price
We need to check the price of the domain before we go further. We can do this with a number of sites.
Looks like it will cost $10.98 to purchase this domain.
Cover Page
We need to find a legit cover page for our domain. We can do this using the “way back machine” (archive.org). This websites takes snapshots of websites overtime. So we should be able to look at an old version of this domain before it expired.
We can download this page source and use it as our cover page. This will help make our domain look legit.
Domain Background Info
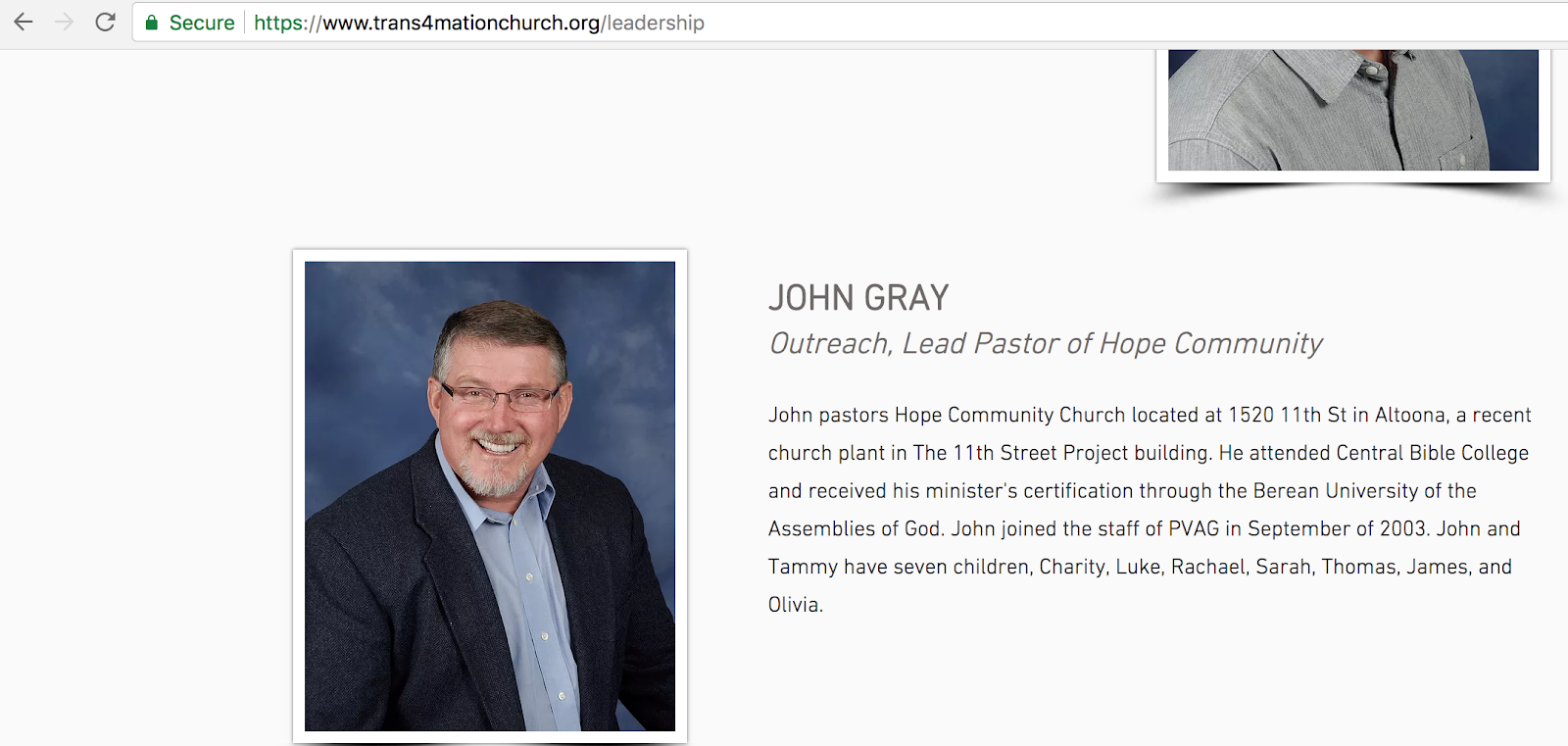
Now we need to do a little bit of research about this domain and its previous owner. I like to find out who previously owned it and if they have a new website set up. This information can be useful to create a better cover story.
Using this information I am able to find the website this organization is currently using “traXXXXXXXXXX.org”.
Fake WHOIS
We have plenty of information to make fake whois information that looks legit. I could use the name “TaXXXX XXay” with the address “15XX 11th st alXXXna, XX XXX01” to buy the domain.
Before I decide to do that I check their new websites “traXXXXXXorg” whois information. It looks like they forgot to use whois privacy so we can see all their information.
It would be better to use this information to buy the domain since it will make our page look that much more legit. Our fake whois information should match their real whois information.
Conclusion
By purchasing an expired domain and dressing it up to look like how it did before it expired and using fake whois information is a really stealthy way to trick investigators. If you saw a domain that has been active for 10 years and matches up with previous versions of that website and the whois information is legit then you might believe that this website is owned by someone else when in fact it isn't. Everything in our website is legit and it could be very hard to tell that it is fake.
Comments
Post a Comment