Introduction
IOT devices need a way to communicate with each other and there are several protocols
that allow them to do this. The most popular IOT communication protocols that run over
wifi are HTTP, MQTT, XMPP, and AMQP. All of these protocols have their own weaknesses
but I will be covering the MQTT protocol.
that allow them to do this. The most popular IOT communication protocols that run over
wifi are HTTP, MQTT, XMPP, and AMQP. All of these protocols have their own weaknesses
but I will be covering the MQTT protocol.
Message Queuing Telemetry Transport (MQTT) is a publish subscribe based message
passing protocol. This protocol was invented in 1999 and they didn't really have security
in mind when they were developing it. The MQTT has several design flaws that could
allow hackers to completely take over your devices and perform other unwanted attacks.
MQTT
passing protocol. This protocol was invented in 1999 and they didn't really have security
in mind when they were developing it. The MQTT has several design flaws that could
allow hackers to completely take over your devices and perform other unwanted attacks.
MQTT
Message Queuing Telemetry Transport (MQTT) is a protocol that runs at the application
layer. MQTT was designed to run on IOT devices because of its many benefits such as:
layer. MQTT was designed to run on IOT devices because of its many benefits such as:
- Efficient Information Distribution
- Increased Scalability
- Reduced Network Bandwidth
MQTT is a publish subscribe based message passing protocol. This means that if you want
to send information you publish it to a topic then those who want to retrieve that information
can subscribe to the topic.

Mosquitto
In the picture above there's a temperature sensor. The sensor will publish the current
temperature to the topic “temperature”. The MQTT broker acts as the middleman by
handling the publish and subscribe messages. Since the laptop and mobile device are
subscribed to the “temperature” topic the broker will relay the temperature information
to them.
temperature to the topic “temperature”. The MQTT broker acts as the middleman by
handling the publish and subscribe messages. Since the laptop and mobile device are
subscribed to the “temperature” topic the broker will relay the temperature information
to them.
Mosquitto
Installation
To set up my practice lab I had to install a MQTT broker and client. I will be using the
mosquitto broker and client since they are open source and run on linux. To download the
broker and client type:
mosquitto broker and client since they are open source and run on linux. To download the
broker and client type:
- Broker
- sudo apt-get install mosquitto
- Client
- sudo apt-get install mosquitto-clients
Subscribe/Publish
Subscribe
Using the “mosquitto_sub” utility we can subscribe to a topic. This utility takes the
arguments:
arguments:
- -h
- Ip of broker
- -t
- Topic name
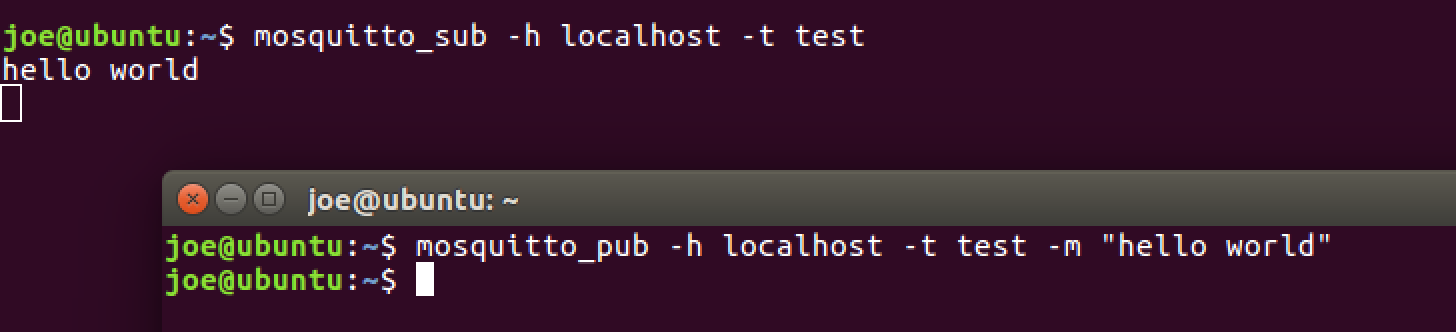
To subscribe to the topic test on our local machine we can type


After looking at shodan a year later we can see that their are now 52,000 MQTT devices.
In just one year 20,000 new MQTT devices were put online. If we take the same stats from
last year than that means 70% of these devices don't use authentication.




“mosquitto_sub -h localhost -t test”.
Publish
Using the “mosquitto_pub” utility we can publush to a topic. This utility takes the arguments:
- -h
- Ip of broker
- -t
- Topic name
- -m
- Data to send
MQTT Design Flaws
Protocol
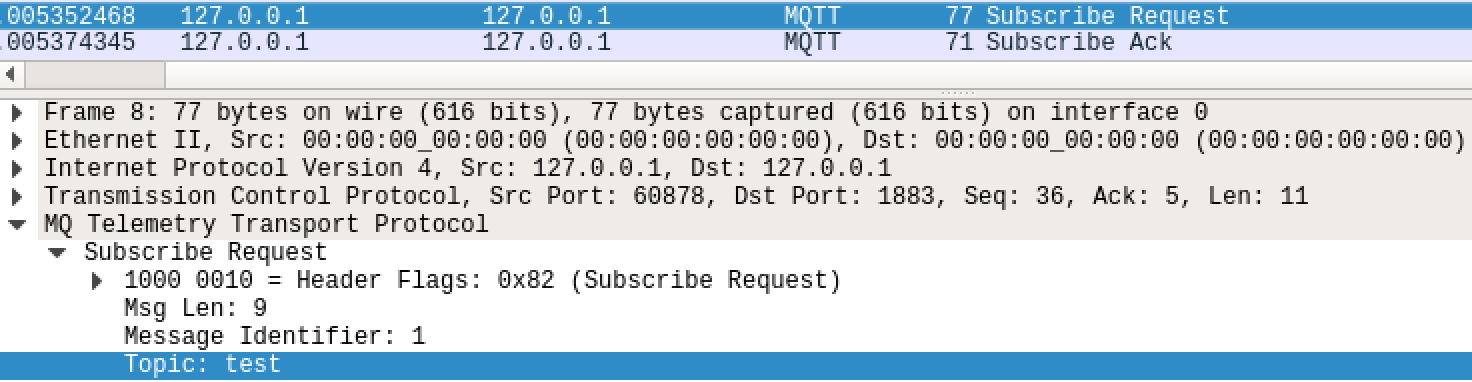
In order to understand the flaws in MQTT we first must understand the protocol itself.
When a client wants to subscribe to a topic it will:
- Connect to broker
- Wait for acknowledgement
- Subscribe to topic
- Wait for acknowledgement
- Receive data from subscribed topic
If a client wants to publish to a topic it must:
- Connect to broker
- Wait for acknowledgement
- Publish data to topic
Authentication
Most of the popular MQTT brokers by default do not require you to submit a password.
This is a huge vulnerability as any one would be able to subscribe and publish to topics.
This could lead to hackers controlling or snooping on your devices. The protocol does
however allow you to authenticate via the connect packet. Even if the client were to use
the optional username and password it would be sent in clear text because encryption is
not supported by this protocol.
This is a huge vulnerability as any one would be able to subscribe and publish to topics.
This could lead to hackers controlling or snooping on your devices. The protocol does
however allow you to authenticate via the connect packet. Even if the client were to use
the optional username and password it would be sent in clear text because encryption is
not supported by this protocol.
Case Study
In 2017 a researcher used shodan and found 32,000 MQTT devices on the internet. He
then created a script to connect to all these devices and looked to see if they had
authentication turned on. He found that 70% of the devices he connected to did not require
authentication.
then created a script to connect to all these devices and looked to see if they had
authentication turned on. He found that 70% of the devices he connected to did not require
authentication.
After looking at shodan a year later we can see that their are now 52,000 MQTT devices.
In just one year 20,000 new MQTT devices were put online. If we take the same stats from
last year than that means 70% of these devices don't use authentication.
Encryption
The MQTT does not provide any kind of encryption. Similar to HTTP if you want to encrypt
your packets you will have to implement SSL/TLS on top of the MQTT protocol. Since this
requires more work most people won't even bother to add encryption.
your packets you will have to implement SSL/TLS on top of the MQTT protocol. Since this
requires more work most people won't even bother to add encryption.
Subscribe/Publish
If someone is able to man in the middle a client then they could view any data that client
receives when they subscribe to a topic. We can even see the topic they subscribe to.
receives when they subscribe to a topic. We can even see the topic they subscribe to.
Username/Password
By default MQTT does not require authentication but if a user wants to they can authenticate
via the connect packet. The only issue is that your credentials will be sent in clear text just
like telnet. If an attacker is sniffing your traffic they will be able to view your username and
password in clear text. We can use “mosquitto_sub” to send a username and password
when subscribing to a topic by using the “-u” and “-P” flag.
via the connect packet. The only issue is that your credentials will be sent in clear text just
like telnet. If an attacker is sniffing your traffic they will be able to view your username and
password in clear text. We can use “mosquitto_sub” to send a username and password
when subscribing to a topic by using the “-u” and “-P” flag.
Conclusion
The MQTT protocol is basically the HTTP of IOT. It shares all of the vulnerabilities that
HTTP, telnet and other old insecure protocols have. Since the protocol was designed back
before security wasn't such an issue its not surprising to see the lack of authentication and
encryption. If people are going to be using this protocol they need to make sure to enable
authentication. In the past year alone 20,000 new devices have been put online. IOT devices
are only getting more popular so we should see the number of MQTT devices rise as well.
In the near feature these devices might become a juicy target due to the number of devices
on the internet and the lack of authentication by default. These combinations will make
MQTT devices low hanging fruit.
HTTP, telnet and other old insecure protocols have. Since the protocol was designed back
before security wasn't such an issue its not surprising to see the lack of authentication and
encryption. If people are going to be using this protocol they need to make sure to enable
authentication. In the past year alone 20,000 new devices have been put online. IOT devices
are only getting more popular so we should see the number of MQTT devices rise as well.
In the near feature these devices might become a juicy target due to the number of devices
on the internet and the lack of authentication by default. These combinations will make
MQTT devices low hanging fruit.
How to make money from betting on football - Work Tomake Money
ReplyDeleteIf you're having problems finding a winning bet 출장안마 online for the day of your choosing, https://jancasino.com/review/merit-casino/ then there are plenty https://deccasino.com/review/merit-casino/ of opportunities febcasino available right งานออนไลน์ here.